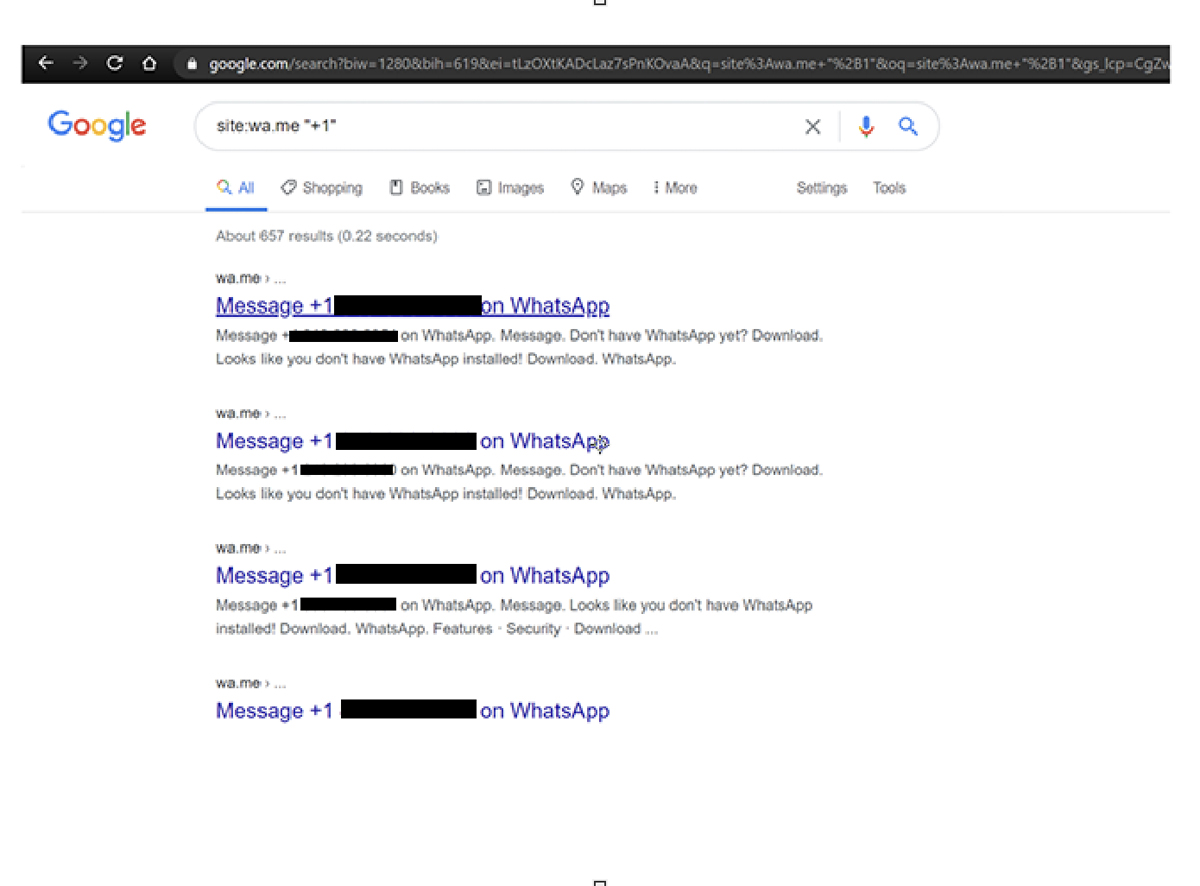
Basically, the feature allows users to begin a chat with someone without having their phone number saved in their contacts. Provided that they know the person’s number and that they have an active WhatsApp account, the user can initiate the chat by creating and providing them a link. Jayaran explained that Click To Chat metadata are indexed by Google, therefore resulting in the “leaking” of user personal information – in this case, their phone numbers – on WhatsApp’s wa.me domain. “Your mobile number is visible in plain text in this URL, and anyone who gets hold of the URL can know your mobile number. You cannot revoke it,” he told Threatpost. The researcher added that he was able to obtain up to 300,000 phone numbers via this vulnerability. He also warned users that this flaw could be exploited by potential attackers or scammers, and could also uncover a person’s identity by referring to their WhatsApp profile. Interestingly enough, WhatsApp has denied Jayaram’s discovery and stated that it is not a flaw whatsoever. They explained that the researcher’s findings contained search engine index of URLs that users have chosen to be made public. Upon contacting the users whose phone numbers were “leaked” in the Google search results, ThreatPost discovered that most of them are well aware that their numbers are made public and it was a way for them to promote their business. However, a small number of users said that they were unaware of this. Meanwhile, Jayaram insists that this issue should be seen as a security flaw and advised WhatsApp to take necessary action in order to prevent potential risks from happening. (Source: ThreatPost via HotHardware)